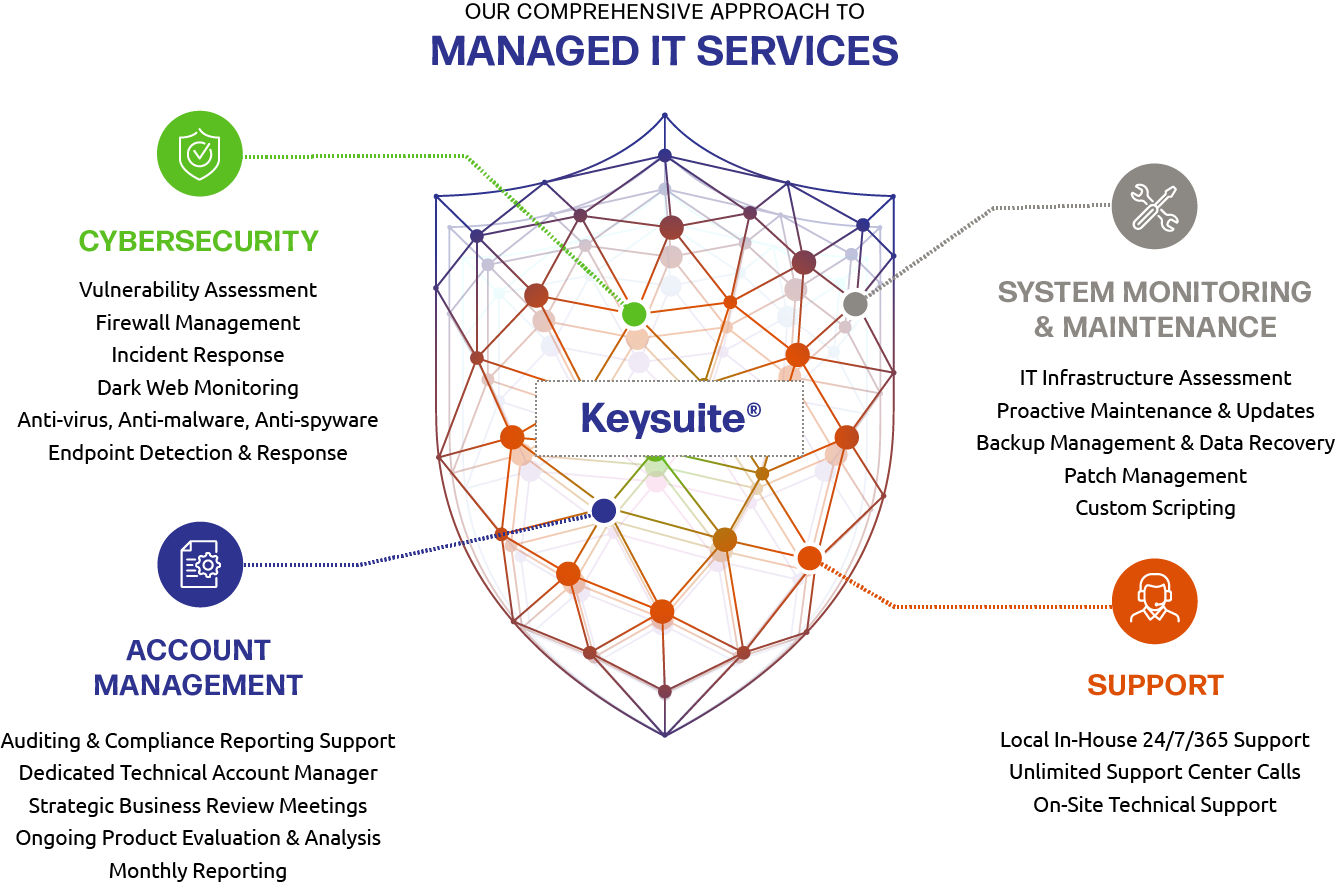
Layered Security: A Robust Cybersecurity Defense System
Businesses are more vulnerable than ever to a myriad of persistent and emerging cyber threats. From data breaches to ransomware attacks, the stakes are high, and the consequences can be devastating. To fortify their defenses, organizations must adopt a layered security strategy that incorporates both technical and organizational controls. These dual pillars work in tandem to create a robust defense against a constantly evolving threat landscape. Read more.